The internet is the textbook definition of “with great power comes great responsibility.” With all the things you can do and discover online, it is easily the greatest information hub that the world has ever known. However, it provides a lot of bad actors the opportunity to take advantage of others. As the internet continues to grow and develop, so do the ways in which spammers can fool you in email attacks. Luckily, there are several lines of defense for protecting yourself and your domain from phishing and spam attacks. This article will discuss SPF, DKIM, and DMARC records and how they help protect your domain.
Spoofing, Phishing, and how they wreak havoc

Have you ever received an email that looked like it came from your boss, but they were urgently asking for iTunes gift cards or your Social Security ID? Or maybe you received a message from Microsoft that had a couple of bizarre typos, but still seems legit. What about the foreign prince who wants to send you five million dollars? That (most likely) was a bad actor trying to pass themselves off as someone else, so they could get sensitive information from you. Spoofing is a type of spam attack in which the bad actor forges parts of their email (usually the From address and Sender’s name) to disguise themselves as someone or something with authority. Spoofing can be similar to the famous ‘Nigerian Prince’ email scam, but generally appears to come from a more “legitimate” sender. Phishing is more advanced, but the intent is still the same. Phishers can attempt to pass off as your university, organization, email provider, and much more by forging full emails, webpages, and/or web links to get you to provide sensitive information.
The importance of being protected from phishing is at an all-time high. CNBC reported that there has been a 61% increase in the rate of phishing attacks since 2021, and AAG reports that 91% of all phishing attacks start with email. With billions of emails being sent daily, major service providers like Google and Yahoo are rolling out stricter security guidelines for users by 2024. Though the stated Google and Yahoo guidelines are tailored for those that send more than 5,000 messages per day, all domain owners should implement the revised guidelines and boost their protection. Also, if you host your domain on Google Workspace, your internal messages will likely count toward the 5,000 daily threshold.
| SPF | DKIM | DMARC |
| A Sender Policy Framework (SPF) is a type of record that defines which mail servers can send and receive mail for your domain. By defining which servers can send and receive mail on your domain’s behalf, receiving servers can verify with SPF that the message has not been forged. An SPF record will define which IP addresses can send mail for the domain, which third-party senders are authorized to send mail, and which servers to reject. If you only send and receive mail from your email account (whether it’s Gmail, Outlook, etc.), you only need to have one third-party defined in your SPF record. However, if you use a third party service for something like marketing blasts, then you will need to include those servers in your record as well. | DomainKeys Identified Mail (DKIM) is another type of record that uses a digital signature to inform the recipient that the message was authorized and sent by the sender. The concept is similar to that of a notary, where the sender has the message authorized (stamped by the notary) and confirmed (entered in the logbook) before it is mailed to the recipient. DKIM protocol uses an encrypted header in the message (the signature) that is decoded by the recipient’s server using an attached public key, which finally authenticates the message for the recipient. DKIM’s authentication method not only ensures that the mail you receive is legitimate, but it also helps prove your outgoing messages’ authenticity as well, thus reducing the chance of your messages being marked as spam. | The latest email authentication method is also one of the most powerful. Domain-based Message Authentication Reporting and Conformance (DMARC) is a protocol established in 2012 that allows you to monitor, review, and take action on suspicious or malicious emails. With a DMARC record, you can choose a policy on what to do if a message fails SPF or DKIM authentication. DMARC can also generate reports for you based on the policies that you set in the record. This provides visibility to the end user on how their domain is being used, ensures the reliability of both incoming and outgoing mail, and keeps organizations in compliance as digital security and government policy adapts. In order to use a DMARC record, you must have at least SPF or DKIM in place (having both is preferred). |
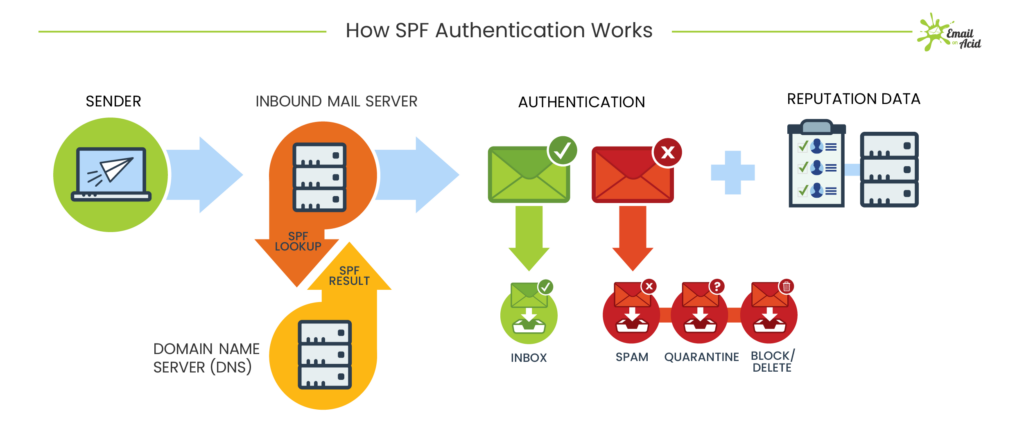
If you already have an SPF or DKIM record in place, then you’re off to a great start. However, no one record will catch everything. Therefore, it is important to authenticate your email with both SPF and DKIM and implement a DMARC policy so you can be as protected as possible. Additionally, it’s very important to know and understand what phishing looks like and how to act if something does get through to your inbox. If you’re unsure of whether these records are in place, drop us a line.
Taking control with Dmarcian
The DMARC protocol is a powerful tool in email authentication. Its ability to review and enact policies to maximize your email safety is impressive, but it does come with some challenges. DMARC’s reporting method is a cumbersome format, so it’s tough to visualize and interpret the data. Additionally, If you work in an organization that sends and receives a high volume of email daily, the default reporting can get overwhelming quickly. Enter Dmarcian: a reporting and management tool developed by one of the DMARC co-authors. Dmarcian takes raw XML data and turns it into detailed reports that you can use to understand your DMARC policy and how it affects email. With Dmarcian, investigating and taking action on your email and domain’s safety is easy and comprehensive. As Dmarcian partners, Umzuzu can help get you started with a free trial of their platform.




