Umzuzu has seen a sudden uptick in phishing scams in recent weeks – as phishing becomes more sophisticated, it is increasingly important to be aware of how phishing adapts and what common themes are.
What is a Nifty scam?
Nifty scams are phishing attempts that normally exploit a vulnerable resource to start their scam – almost always it’s an abuse of nifty.com, a Japanese ISP, and their free email account program. Registering for a free account here gets the bad actor past a major hurdle: verifying their outbound email to receiving servers. By using Nifty, the bad actors don’t have to spoof a domain – instead, they’re legitimately using the authentication that is built into Nifty’s framework. Much like by using a free Gmail account, you don’t have to set up your own DNS records for authentication.
It starts with the bad actor identifying their target, then creating a Nifty account that they can use to lure in the hopeful victim. As you can see from this example below that I actually received, they tried to use a bogus email using the Umzuzu name:
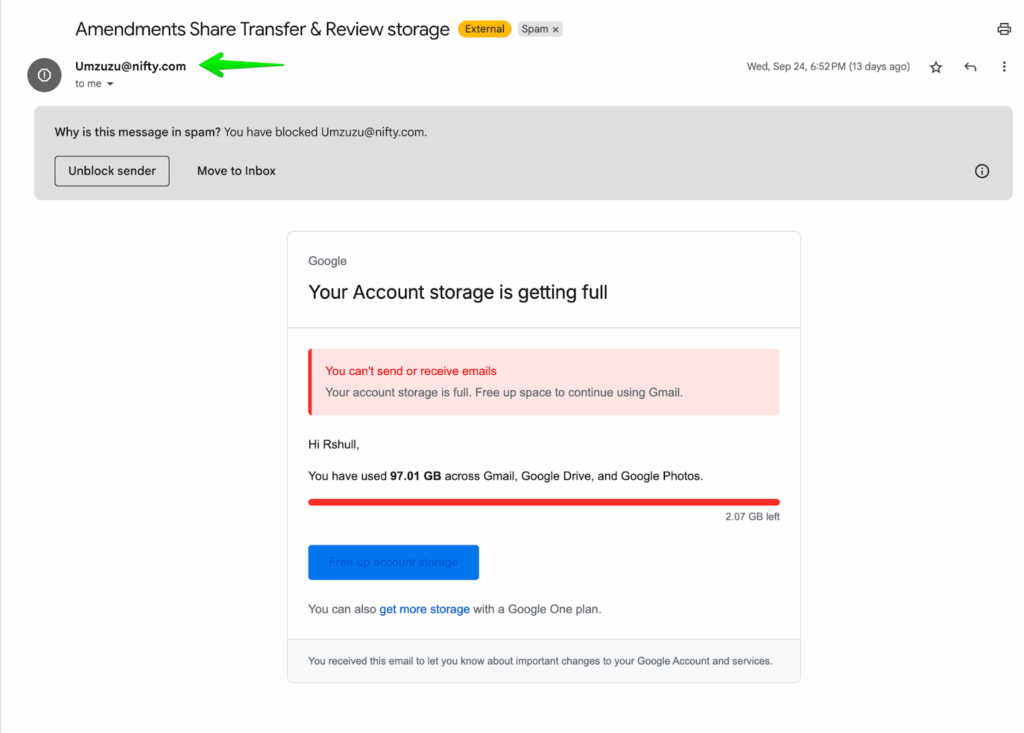
Next, the message. Phishing scams try to trick you into thinking that they are who they say they are. That involves using some sort of persuasion – whether urgency, authority, or similar – to get you to follow the link and submit your information. In the above example, you can see that they’re trying to pass themselves off as Google with the urgent message that I’m almost out of storage. They want me to click the blue button to free up more storage, which this email obviously isn’t going to help me with. Another Nifty scam example is below:
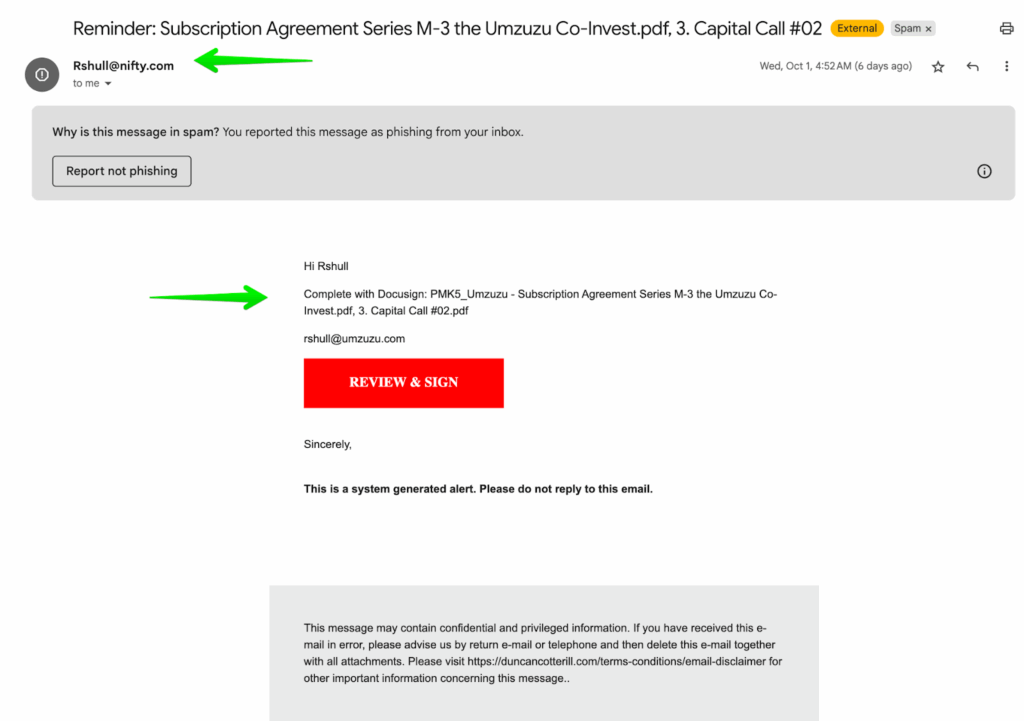
In this one, you can see that they’re trying to copycat my email username, and also get me to complete a Docusign file (that definitely doesn’t exist).
The last part of the scam is the part where they capture your information. If you do follow the link, you will ultimately be routed to a page that continues the charade, and asks you to input your account credentials. That’s where they get you – a phony login field that captures your details and essentially gives them the keys to the safe.
Docusign, Google, Microsoft, and Dropbox are four of the most common brands that these scammers mimic to try to get their victims to input information.
What happens if someone’s account is breached? Depending on the hacker’s intent, several things could happen. Normally, these hackers are trying to get the scam spreading like a virus, so they’ll first go after your contacts list and send a very similar scam message pretending to be you. But, data loss can occur as well if they decide to pilfer through your inbox.
There are several ways to protect yourself from these attacks:
- Recognize the signs – the nifty.com email address, errors in spelling or grammar, poor formatting
- Not expecting it? Don’t open it!
- If you’re not expecting to get a Docusign, Google, Dropbox, or other message, or if someone you haven’t been in contact with for a long time sends you “something to sign,” proceed with extreme caution, and don’t click on any links or attachments until you know the email is safe.
- Deploy 2-Step Verification
- One of the best defenses against account breaches, and it’s built into your Workspace or Microsoft functionality as well.
- Install a third party spam filter – We recommend our partner service Check Point’s Harmony email filter to help process & clear out spam messages before they hit your inbox.
If you have any questions about spam and how to protect your organization, drop us a line.



